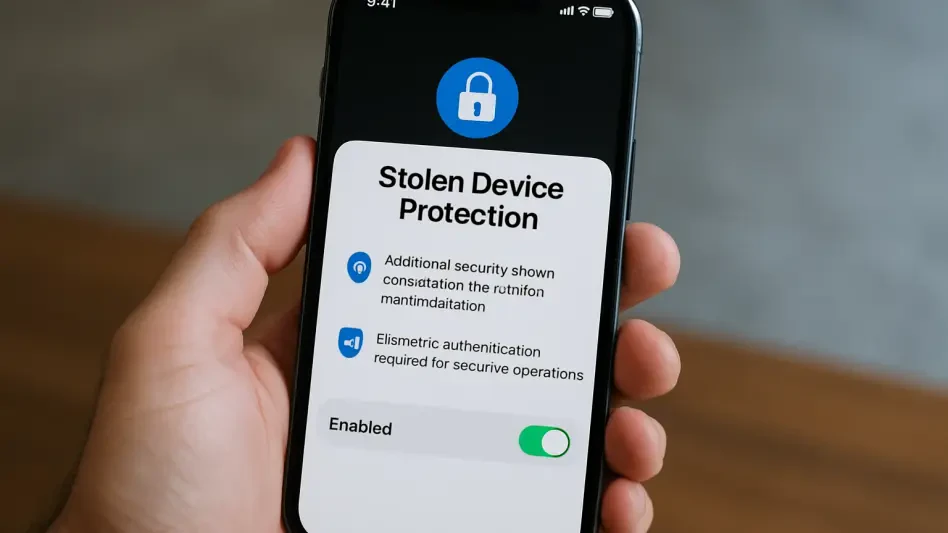
Hidden iOS Feature Stops iPhone Data Theft in Its Tracks
Imagine walking through a crowded city street, only to feel a sudden tug as your iPhone slips from your pocket, vanishing into the hands of a thief who now holds the key to your digital life.
Read More