Threats and Vulnerabilities

Threats and Vulnerabilities
How Do Low-Skill Hackers Damage Critical Systems?
The prevailing image of a state-sponsored cyberattack often involves highly sophisticated teams deploying zero-day exploits, but a more insidious and chaotic threat is emerging from the digital shadows, proving that even rudimentary skills can jeopar...
Industry Report Read More Threats and Vulnerabilities
Trend Analysis: Nation-State Cyber Operations
The once-clear line separating digital skirmishes from tangible geopolitical conflict has effectively vanished, ushering in a new and more volatile era of strategic competition where the keyboard has become as mighty as the sword.
Trend AnalysisTrending
Read More Threats and Vulnerabilities
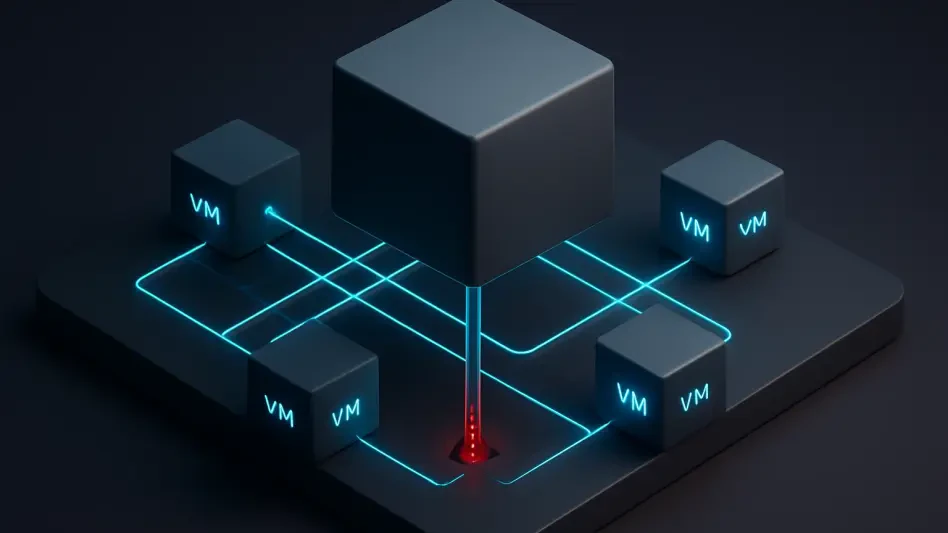
Can a Proxmox Host Silently Control Your VMs?
The modern data center relies heavily on virtualization, a technology that isolates workloads into secure virtual machines, with the hypervisor acting as an impenetrable barrier between them.
Read More Threats and Vulnerabilities
Microsoft Patches Windows Zero-Day Under Active Attack
In a stark reminder of the persistent threats facing modern operating systems, Microsoft has issued an emergency security update to address a critical zero-day vulnerability that is already being actively exploited in the wild by malicious actors.
Read More Threats and Vulnerabilities
Ransomware Shifts to Extortion as Defenses Improve
As cybersecurity shields grow stronger within the manufacturing sector, a more sinister threat has emerged from the shadows, transforming ransomware from a simple digital lockdown into a complex campaign of public extortion.
Research Summary Read More Threats and Vulnerabilities
Why Is React2Shell a Perfect Storm for Security?
A technology designed to accelerate web development and enhance user experience has inadvertently become one of the most significant security threats of the year, demonstrating how quickly innovation can be weaponized against the very systems it was...
Interview Read More Threats and Vulnerabilities
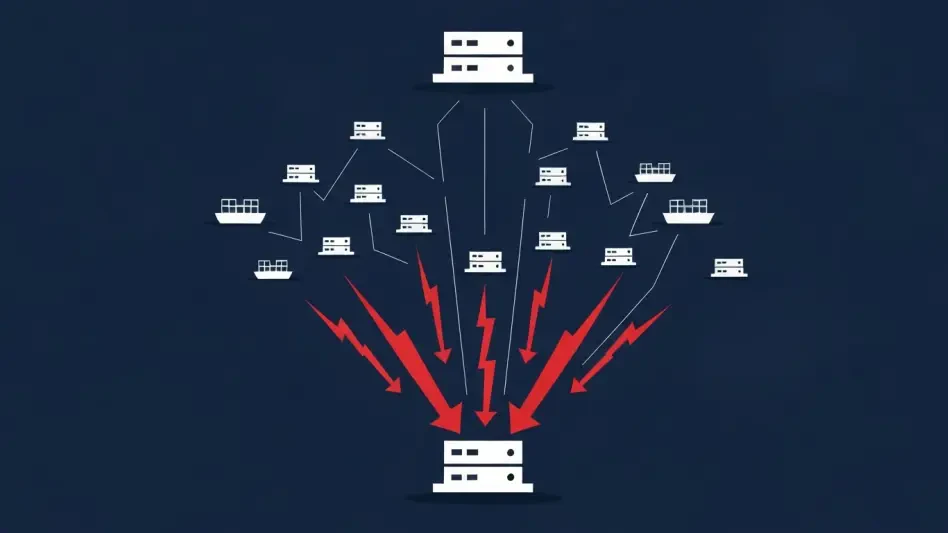
How Was React2Shell Weaponized in Just Minutes?
The established timeline for vulnerability disclosure and exploitation has been irrevocably shattered, with the gap between a flaw’s public announcement and its active weaponization now being measured in minutes rather than days or weeks.
Read More Threats and Vulnerabilities
Trend Analysis: Cyber-Enabled Kinetic Targeting
The alarming speed with which state-sponsored threat actors began exploiting the "React2Shell" vulnerability immediately following its public disclosure marks a definitive shift in the landscape of international cyber warfare.
Trend Analysis Read More
Get our content freshly delivered to your inbox. Subscribe now ->
Receive the latest, most important information on cybersecurity.