Operational Technology environments, which form the digital backbone of critical infrastructure like power grids and water treatment facilities, present a formidable and high-stakes cybersecurity challenge unlike any other. The immense cost of specialized hardware and the unacceptable risk of disrupting vital physical processes make hands-on security training on live Industrial Control Systems (ICS) almost entirely impractical. This creates a dangerous knowledge gap, leaving security teams with theoretical knowledge but little to no practical experience in defending against sophisticated cyber-attacks that can cause real-world physical damage. Advanced, high-fidelity simulators are now emerging as an indispensable solution, offering a safe, accessible, and realistic way for professionals to build the muscle memory and hands-on skills required to protect these essential systems from an evolving landscape of digital threats.
Bridging the Gap with Accessible Virtual Labs
A primary obstacle in strengthening OT security has long been the prohibitive cost and limited availability of physical industrial hardware for training purposes, effectively creating a high barrier to entry for aspiring and current cybersecurity professionals. To dismantle this barrier, organizations are pioneering the development of open-source, software-based simulation platforms that democratize access to realistic OT environments. By creating virtual sandboxes that replicate the intricate interactions of control hardware and industrial processes, these tools provide a cost-effective alternative to building and maintaining expensive physical labs. This approach allows security teams, researchers, and students to freely experiment, test defensive strategies, and simulate attack scenarios without any risk to live operations. The availability of these tools signifies a critical shift, enabling a much broader community to gain the practical, hands-on experience needed to understand and protect complex industrial control systems from cyber threats.
Simulating Real-World Processes and Protocols
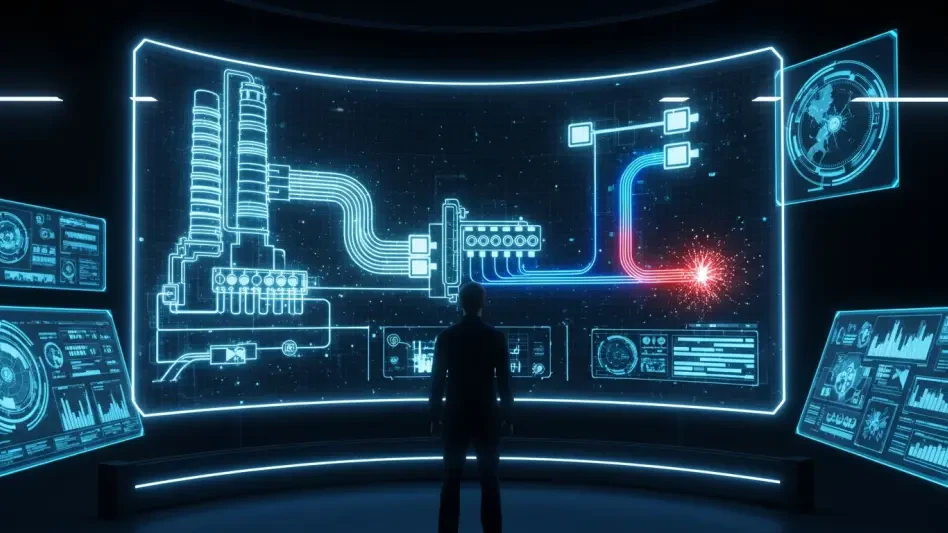
The true value of these training platforms is rooted in their ability to meticulously model the behavior of real-world industrial operations and their underlying communication protocols. A prime example is a simulator that emulates a complete water treatment system, featuring a virtual PLC-style server that manages inflows, outflows, operating modes, and alarms, all of which are visualized through a web-based Human-Machine Interface (HMI). What makes such a tool profoundly effective is its native support for widely used industrial protocols like Modbus and BACnet, allowing trainees to interact with the simulated system using the same commands and techniques an adversary would employ. This design intentionally creates a transparent and observable control loop, clearly demonstrating the direct cause-and-effect relationship between specific protocol-level actions and their tangible impact on the physical state of the industrial process, thereby cementing a deeper understanding of system vulnerabilities.
From Theory to Practice Through Adversary Emulation
Modern simulators transform passive, theoretical learning into an active, hands-on experience by enabling sophisticated adversary emulation within a controlled environment. When integrated with automation frameworks, these virtual labs allow users to execute pre-built or custom attack scenarios that mirror the tactics, techniques, and procedures used by real-world threat actors. A training session can begin with foundational reconnaissance techniques, such as using a Discovery module to identify simulated devices on the network or employing a Collection tactic to read critical process values like a water tank level or flow rate. From there, trainees can escalate their actions to simulate a direct attack, leveraging techniques under the Impair Process Control category to manipulate the system. This could involve sending a malicious Modbus or BACnet command to switch the system into a manual override mode, directly setting flow rates to trigger an overflow condition, or issuing an emergency stop command to halt the entire process.
Visualizing Impact to Refine Defensive Postures
The most vital lesson that these simulated environments provided was the ability to directly observe the tangible consequences of a cyber-attack in real time, a perspective that is nearly impossible to gain otherwise. When a trainee executed a malicious command, the simulator’s HMI offered immediate and unambiguous visual feedback—a tank level was seen rising toward a critical threshold, an alarm light began to flash on the screen, or a pump icon visibly changed its operational state. By capturing and analyzing the underlying network traffic responsible for these changes, defenders learned to correlate specific, anomalous protocol packets with their potential physical impact. This direct, hands-on experience, which connected a cyber event to a physical outcome, proved invaluable for developing and validating more effective monitoring rules, honing incident response playbooks, and ultimately building more resilient defensive strategies for protecting live OT environments from harm.