What could be more enticing to cybercriminals than industrial control systems regulating critical infrastructure, and how can network segmentation serve as an impenetrable shield against these threats?
The Growing Threat to Industrial Systems
The rise in cyber threats targeting operational technology (OT) and industrial control systems (ICS) has become a pressing concern for industries worldwide. These systems, often connected to enterprise IT environments, are increasingly vulnerable to sophisticated attacks that can halt production, compromise safety, and disrupt business continuity. This exposure underscores the need for robust cybersecurity measures that go beyond traditional defenses, emphasizing the critical nature of network segmentation in safeguarding these vital systems.
Network Segmentation: Functionality and Challenges
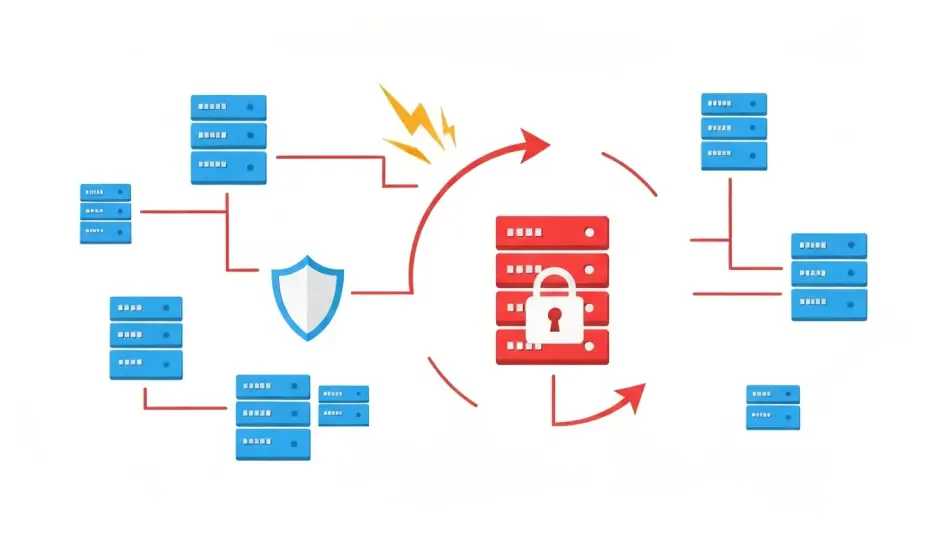
Network segmentation acts as a powerful tool by limiting the lateral movement of attackers, which restricts their ability to traverse the network unchecked. It enhances visibility and control over critical assets, allowing organizations to enforce policies and detect threats more effectively. However, integrating cutting-edge security solutions with legacy ICS brings its own set of challenges. Thorough risk assessments and stakeholder collaboration are paramount to ensure seamless execution. Real-world applications demonstrate the success of network segmentation in isolating and protecting critical assets while allowing uninterrupted operations.
Expert Insights on Cybersecurity Strategies
Leading cybersecurity experts such as Jonathon Gordon, Andrew McPhee, Mark Toussaint, and Tom Sego have shed light on the importance of layering security to defend industrial systems. Their insights highlight the role of firewalls, intrusion detection/prevention systems (IDS/IPS), and sophisticated segmentation techniques. Practical case studies further illustrate how these measures can be implemented successfully, reinforcing the view that combining perimeter controls with network segmentation is essential for robust OT security.
Jonathon Gordon emphasizes the significant advancements in protecting OT/ICS through stringent perimeter security and network segmentation. Andrew McPhee focuses on how segmentation disrupts attackers’ lateral movement, making a breach significantly harder. Mark Toussaint discusses the effectiveness of multiple layers of security, including diverse types of segmentation, while Tom Sego highlights software-defined segmentation’s efficiency in securing vulnerable OT devices.
Practical Steps for Effective Network Segmentation
To achieve successful network segmentation, organizations should follow a step-by-step approach that includes conducting thorough risk assessments, creating effective policies, and ensuring restricted, time-bound access for remote users. Advanced techniques such as software-defined segmentation, identity-based access controls, and multi-factor authentication are pivotal. Balancing security with operational continuity requires continuous monitoring and real-time threat detection, alongside zero trust architecture principles that prioritize robust defense mechanisms.
A systematic strategy begins with detailed risk assessments to pinpoint vulnerabilities. Crafting precise policies ensures minimal operational disruption while maintaining security. Remote access must be strictly controlled, and advanced technologies like software-defined segmentation offer dynamic control over network partitions. Continuous monitoring is critical to detect and resolve threats instantly, embodying the zero trust principle of never assuming safety without verification.
Conclusion
The growing cyber threats have necessitated robust defenses for industrial systems, with network segmentation and perimeter strategies forming the backbone of this protective framework. By integrating zero trust principles and modern technical approaches, industries can ensure enhanced security without compromising operational continuity. The collaborative efforts among stakeholders, coupled with comprehensive risk assessments, can effectively mitigate potential risks.
The financial and operational benefits of these cybersecurity investments far outweigh their costs, emphasizing their importance in long-term risk management. Thus, moving forward, the integration of advanced segmentation techniques with zero trust architectures remains essential for safeguarding critical industrial systems, ensuring resiliency against ever-evolving cyber threats.