In an era where digital security is paramount, password managers have become indispensable tools for millions, entrusted with protecting everything from login credentials to credit card details and personal data. However, a startling revelation by cybersecurity researcher Marek Tóth has exposed critical zero-day vulnerabilities in eleven leading password managers, including industry giants like 1Password, LastPass, and Bitwarden.
Understanding the Threat
Decoding the Attack Mechanism
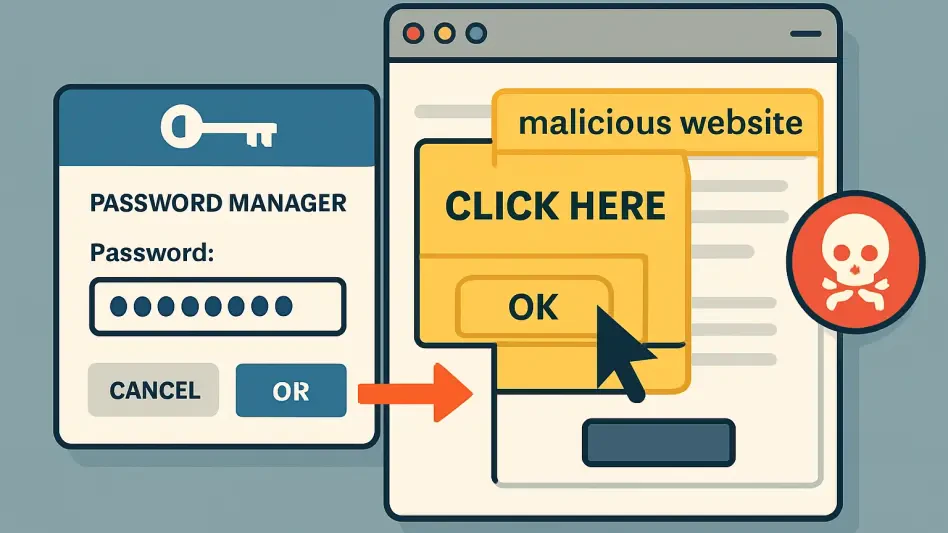
The heart of this vulnerability lies in a cunning method called DOM-based Extension Clickjacking, which exploits the user interface elements that password managers integrate into web pages. Unlike traditional clickjacking tactics that rely on hidden iframes, this approach uses JavaScript to manipulate the Document Object Model (DOM), rendering clickable components invisible through techniques like opacity tweaks or overlays. Attackers craft malicious or compromised websites where a user’s innocent click—perhaps on a seemingly benign button—triggers the hidden interface, silently extracting stored data such as passwords or sensitive details. This client-side exploit bypasses conventional web security measures, making it particularly insidious as it targets the very convenience features, like autofill, that users depend on daily. The technical sophistication of this attack underscores a growing trend in cyber threats, where attackers innovate to exploit trust in familiar digital interactions.
Why This Exploit Is Unique
What sets DOM-based Extension Clickjacking apart is its ability to operate within the trusted environment of browser extensions, turning a security tool into a potential liability. This method doesn’t require complex server-side breaches; instead, it manipulates the front-end experience, deceiving users into actions they believe are safe. The attack’s effectiveness lies in its subtlety—users remain unaware that their data has been compromised, as there are no overt signs of intrusion like pop-ups or redirects. Moreover, this vulnerability affects a wide range of data types, from login credentials to two-factor authentication (2FA) codes, amplifying its danger. Standard defenses like HTTP headers, such as X-Frame-Options, prove ineffective against these client-side manipulations, highlighting a critical gap in current security frameworks. This evolving threat demands a reevaluation of how browser extensions are designed and protected against such deceptive tactics.
Scale and Impact
Quantifying the Global Risk
The sheer scale of this cybersecurity flaw is alarming, with around 40 million active installations of password managers across platforms like Chrome, Firefox, and Edge found to be at risk. Testing revealed that all eleven major tools analyzed were susceptible to at least one variant of the DOM-based attack, exposing users to severe consequences. Credential theft was possible in ten of these tools, while eight allowed extraction of personal information, and six left credit card data vulnerable. Even Time-based One-Time Password (TOTP) codes, a key component of 2FA, were not spared, with several managers failing to secure this critical safeguard. This widespread exposure paints a sobering picture of systemic vulnerability, where millions of users, unaware of the lurking danger, continue to rely on compromised tools for their digital security, emphasizing the urgent need for awareness and action.
Beyond Numbers: Real-World Consequences
While the statistics are staggering, the real-world implications of these vulnerabilities are even more unsettling. A single click on a malicious site could lead to identity theft, financial loss, or unauthorized access to critical accounts, impacting both individuals and businesses. The ripple effects extend further, as stolen credentials often fuel broader cybercrimes like phishing campaigns or data breaches on a massive scale. Additionally, the trust users place in password managers as a cornerstone of their security strategy is undermined, potentially eroding confidence in digital tools altogether. For organizations, the risk of compromised employee accounts could lead to breaches of sensitive corporate data, amplifying the stakes. This situation serves as a stark reminder that cybersecurity is not just a technical issue but a deeply personal and economic concern, affecting lives in tangible ways beyond mere numbers on a report.
Attack Vectors
Malicious Sites as Entry Points
One of the primary ways DOM-based Extension Clickjacking manifests is through fully attacker-controlled websites designed to deceive users. These sites often mimic legitimate platforms or present familiar prompts like login forms, cookie consent banners, or CAPTCHA challenges, luring users into clicking on seemingly harmless elements. Beneath the surface, hidden UI components of password managers are triggered, automatically filling in sensitive data that attackers can harvest. The simplicity of this vector makes it highly effective, as it preys on routine online behavior without requiring sophisticated user manipulation. Given the proliferation of malicious websites, often distributed through phishing emails or deceptive ads, this attack method poses a constant threat to unsuspecting users who may not recognize the danger until it’s too late, highlighting the deceptive nature of modern cyber traps.
Exploiting Trusted Domains
Even more insidious are attacks that leverage trusted domains through subdomains exploited via Cross-Site Scripting (XSS) or subdomain takeovers, expanding the threat landscape significantly. Password managers frequently autofill data across all subdomains of a saved website, a feature meant for convenience but now a glaring weakness. Attackers can compromise a subdomain of a familiar site, embedding malicious code that triggers the same clickjacking mechanism without raising suspicion. Users, seeing a recognizable domain, are less likely to question interactions, making this vector particularly dangerous. The trust in established websites becomes a double-edged sword, as attackers exploit this confidence to execute seamless data theft. This scenario underscores how vulnerabilities can hide in plain sight, turning even reputable digital spaces into potential battlegrounds for cybersecurity risks.
Vendor Response
Progress and Delays in Fixes
Following the responsible disclosure of these vulnerabilities in April of this year, the response from password manager vendors has been uneven, reflecting the complexity of addressing such flaws. Companies like Dashlane, Keeper, NordPass, ProtonPass, and RoboForm acted relatively swiftly, deploying patches to mitigate the risk for their users. However, major players such as 1Password, LastPass, Bitwarden, iCloud Passwords, Enpass, and LogMeOnce—collectively representing about 32.7 million active installations—remained vulnerable as of August. This delay points to the intricate challenge of securing browser extensions against client-side exploits, which cannot be fully countered by traditional web security protocols. The disparity in response times leaves a significant portion of users exposed, raising concerns about prioritization and resource allocation among vendors in tackling urgent security threats.
Challenges in Securing Extensions
The slow pace of remediation among some vendors highlights broader technical hurdles in safeguarding browser extensions, which are deeply integrated into web environments. Unlike server-side vulnerabilities, client-side attacks like DOM-based Extension Clickjacking require innovative defenses at the extension level, often necessitating extensive redesigns or updates to core functionalities. Standard web security measures, such as Content-Security-Policy headers, fall short against these threats, complicating the development of effective patches. Additionally, vendors must balance the urgency of fixes with thorough testing to avoid introducing new issues, a process that can delay deployment. For users relying on unpatched tools, this lag translates into prolonged risk, emphasizing the need for industry-wide collaboration to establish faster, more robust response mechanisms for emerging extension-based vulnerabilities.
User Protection
Practical Steps for Immediate Safety
In the absence of universal fixes, users must adopt proactive measures to shield themselves from these clickjacking vulnerabilities, even if such steps come at the cost of convenience. One effective approach is adjusting extension settings in Chromium-based browsers to require manual permission for site access, rather than granting automatic access, which limits unauthorized interactions. Keeping password manager software updated is also critical, as patches—when released—can address known flaws. Additionally, disabling manual autofill features, though inconvenient, reduces the risk of data being automatically inserted into malicious forms. These actions, while not entirely foolproof, create a temporary barrier against attacks, buying time until developers implement comprehensive solutions. User vigilance in scrutinizing unfamiliar prompts or websites further complements these technical adjustments.
Balancing Security and Usability
Adopting protective measures often forces users into a difficult trade-off between security and ease of use, a dilemma that underscores the broader challenge of digital safety. Disabling autofill or restricting extension access can slow down online tasks, frustrating users accustomed to seamless experiences. Yet, the potential consequences of data theft—ranging from financial loss to identity compromise—far outweigh temporary inconvenience. Educating oneself about safe browsing habits, such as avoiding clicks on suspicious links or prompts, adds another layer of defense. Until vendors close the security gaps, users bear a significant share of responsibility in navigating this threat landscape. This balance between precaution and practicality serves as a reminder that cybersecurity is a shared endeavor, requiring both individual caution and systemic improvements to ensure long-term protection against evolving risks.