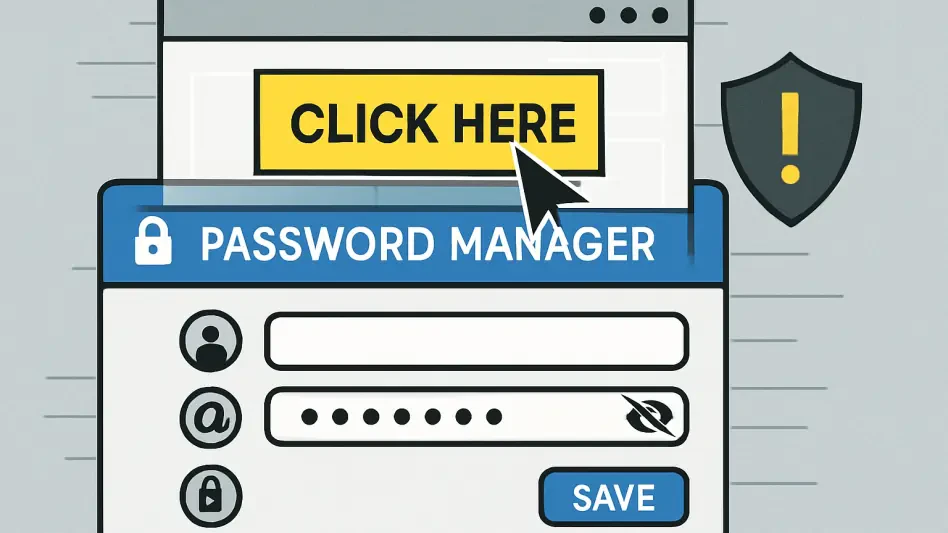
In an era where digital security is paramount, password managers have become indispensable tools for safeguarding sensitive information like login credentials and financial data, but recent findings have unveiled a disturbing vulnerability that threatens their very purpose. A sophisticated technique known as DOM-based clickjacking can manipulate certain password managers into autofilling credentials into fraudulent forms on malicious websites, exposing users to significant risks. This exploit operates stealthily, often without any indication to the user that their data has been compromised. As cyber threats continue to evolve, understanding these vulnerabilities and implementing protective measures is crucial for anyone relying on password managers to secure their online presence. This article delves into how this attack functions and offers practical steps to mitigate the dangers posed by such exploits, ensuring that digital safety remains a priority in an increasingly complex threat landscape.
1. Understanding the Threat of DOM-Based Clickjacking
The foundation of the DOM-based clickjacking attack lies in a clever exploitation of the Document Object Model (DOM), a structure that browsers use to render webpages. Malicious actors create a variant of clickjacking that secretly triggers the autofill feature of password managers, allowing them to harvest sensitive information such as passwords, two-factor authentication (2FA) codes, and credit card details. The attack begins when a user visits a compromised webpage displaying seemingly harmless elements like a cookie consent banner or a “close” button on a pop-up. Unbeknownst to the user, an invisible form is positioned over the clickable area through DOM manipulation, often by setting opacity to zero. When the user interacts with the element, the password manager extension automatically populates the hidden form with credentials, which are then captured by the attacker. This process happens without any visible cues, making it a particularly insidious threat to digital security.
Even more concerning is the scope and persistence of this vulnerability across various password management tools. Testing on multiple popular password managers revealed that many are susceptible to this attack, despite some vendors releasing patches to introduce confirmation prompts for autofill actions. However, these patches often serve as temporary fixes rather than comprehensive solutions. The root issue stems from how browsers render webpages, a factor largely outside the control of browser extensions. As a result, even updated password managers may still be at risk, underscoring the need for users to adopt additional safeguards. Recognizing the mechanics of this exploit is the first step toward protecting against it, as it highlights the importance of scrutinizing the default behaviors of security tools and adjusting settings to minimize exposure to such advanced cyber threats.
2. Disabling Autofill to Prevent Exploitation
One of the most effective ways to counter DOM-based clickjacking is to disable the autofill feature in password manager extensions, as this function is the primary target of the attack. By default, many password managers automatically populate fields when a user clicks on them, creating an opportunity for malicious forms to capture data. Turning off this setting ensures that credentials are not entered without explicit user consent, significantly reducing the risk of unauthorized access. To implement this, users should navigate to the settings of their password manager extension and locate the autofill or similar section, where a toggle to disable automatic filling on focus can usually be found. This adjustment forces a manual action to input data, adding a critical layer of control over when and where sensitive information is shared.
While disabling autofill may introduce a slight inconvenience, the security benefits far outweigh the extra effort required to manually trigger credential entry. After making this change, users will typically need to click a specific button or icon when a field is selected to populate it with stored data. This manual process acts as a safeguard against hidden forms on malicious sites, ensuring that password managers do not inadvertently expose information. Importantly, this step does not diminish the core functionality of password managers as secure storage solutions; it simply shifts the responsibility of data entry back to the user. By taking this precaution, individuals can maintain the utility of their security tools while mitigating one of the most exploitable features targeted by clickjacking attacks, thereby enhancing overall digital protection.
3. Limiting Extension Access for Added Security
Another vital measure to protect against clickjacking involves configuring browser extensions to operate only under specific conditions, such as on designated websites or when manually activated. Most modern browsers offer settings that allow users to control extension behavior, preventing password managers from functioning on unfamiliar or untrusted sites where malicious code might reside. To apply this safeguard, access the browser’s Extensions page, locate the details for the password manager, and adjust the “Site Access” settings. Options like “On Click” ensure the extension activates only when the toolbar icon is clicked, while “On Specific Sites” restricts activity to pre-approved domains. This customization requires some initial setup but offers a robust defense against unauthorized autofill triggers on malicious pages.
Implementing these restrictions not only reduces the attack surface but also fosters a more mindful approach to online security. By limiting where and how a password manager operates, users can avoid scenarios where a seemingly innocent click on a deceptive element leads to credential theft. Although this may mean an additional step or two when accessing trusted sites, the trade-off is a significant decrease in vulnerability to DOM-based exploits. This approach complements other protective measures by ensuring that even if a malicious site attempts to exploit autofill capabilities, the extension remains inactive unless explicitly authorized. As cyber threats grow more sophisticated, tailoring extension permissions to align with specific usage patterns becomes an essential strategy for maintaining control over sensitive data in the digital realm.
4. Opting for Desktop and Mobile Apps Over Extensions
For those seeking to minimize risks associated with browser-based clickjacking attacks, transitioning from extensions to desktop or mobile apps offered by password managers presents a viable alternative. These attacks predominantly target browser extensions due to their integration with webpages and autofill functionalities, leaving standalone apps less exposed to such threats. Desktop and mobile applications typically provide features like search and copy functions, enabling users to manually retrieve and input credentials without the automated risks inherent in browser extensions. This method ensures that sensitive data is not automatically inserted into potentially compromised forms, offering a safer way to manage passwords while retaining the convenience of a centralized vault.
Adopting standalone apps also encourages a more deliberate interaction with login processes, further reducing the likelihood of falling victim to stealthy exploits. When accessing a login page, users can simply search for the relevant entry in the app, copy the credentials, and paste them into the required fields. This manual approach circumvents the vulnerabilities tied to browser rendering and extension permissions, providing a secure workaround without sacrificing the core benefits of password management. While it may require adjusting to a slightly different workflow, the shift to apps represents a proactive step in safeguarding personal information against the specific mechanisms of DOM-based clickjacking. As threats evolve, leveraging these alternative platforms can serve as a critical component of a comprehensive security posture.
5. Blocking Scripts to Thwart Malicious Code
A powerful defense against clickjacking and similar cyber threats is the use of script blocker extensions, which prevent on-page scripts from executing on untrusted websites. Many attacks, including DOM-based exploits, rely heavily on JavaScript and other active scripts to manipulate webpage elements and trigger unauthorized actions like autofill. By installing a tool such as NoScript, available for browsers like Chrome and Firefox, users can block all scripts by default and selectively enable them only on trusted domains. This approach disrupts the operational foundation of clickjacking attacks, rendering malicious forms and hidden elements ineffective since the underlying code cannot run without explicit permission, thus protecting sensitive data from being harvested.
Incorporating script blockers into a security toolkit not only counters specific threats like clickjacking but also enhances overall online safety by limiting exposure to a wide range of script-dependent attacks. Configuring such extensions to allow scripts solely on verified websites ensures that untrusted or unfamiliar domains cannot execute potentially harmful code. While this may initially require some adjustment to whitelist frequently visited sites, the added protection against unauthorized data access is well worth the effort. This strategy works in tandem with other protective measures, creating multiple layers of defense that collectively reduce the risk of credential theft. As cybercriminals continue to exploit browser functionalities, blocking scripts stands out as a fundamental tactic to maintain control over personal information in an increasingly hostile digital environment.
6. Strengthening Account Security with Robust Authentication
Beyond adjusting password manager settings, fortifying account security with strong secondary authentication methods remains a cornerstone of protection against credential theft. Implementing 2FA with a Time-Based One-Time Password (TOTP) app, ideally on a separate device, adds a critical barrier that attackers cannot easily bypass, unlike less secure options such as SMS verification. For even greater security, adopting passkeys or hardware security keys offers a superior alternative to traditional 2FA, as these methods tie authentication to physical devices or unique cryptographic tokens. Such measures ensure that even if passwords are stolen through clickjacking or other means, unauthorized access to accounts remains highly unlikely without the secondary factor.
Additionally, minimizing reliance on automatic login solutions can further shrink the attack surface for potential exploits. While the convenience of autofill and similar features is undeniable, the slight inconvenience of manual entry or additional authentication steps pales in comparison to the risk of data breaches. Users should prioritize security over speed, especially when storing highly sensitive information in password managers. Combining robust authentication with cautious usage habits creates a formidable defense against a range of cyber threats, not just clickjacking. By integrating these practices, individuals can confidently navigate the digital landscape, knowing that their accounts are safeguarded by multiple layers of protection tailored to counter evolving attack methodologies.
7. Taking Action to Secure Digital Assets
Reflecting on the vulnerabilities exposed by DOM-based clickjacking, it becomes clear that password managers, while invaluable, are not immune to sophisticated cyber threats. The stealthy nature of these attacks, which exploit autofill features through hidden forms, catches many users off guard, highlighting the need for heightened vigilance. In response, steps should be taken to address these risks head-on, ensuring that tools meant to enhance security do not inadvertently become liabilities. The urgency to adapt to such threats underscores the importance of staying informed about emerging exploits and the limitations of even the most trusted applications in the face of innovative attack vectors.
Looking ahead, actionable measures provide a clear path to bolster defenses against these risks. Disabling autofill, restricting extension access to trusted sites, opting for standalone apps, employing script blockers, and reinforcing accounts with strong 2FA or hardware keys emerge as essential strategies. These steps, though requiring some adjustment, offer practical ways to mitigate vulnerabilities without abandoning the benefits of password management. As cyber threats continue to evolve, regularly reviewing and updating security practices will remain vital to protecting digital assets. Staying proactive with these safeguards ensures that personal data stays secure in an ever-changing landscape of online risks.