The seamless flow of clean water from a tap or the steady hum of electricity powering communities relies on a complex and often vulnerable network of industrial controls, a reality that has been brought into sharp focus by a recent wave of cyber intrusions. Global cybersecurity agencies have issued a stark warning about the escalating activities of pro-Russia hacktivist groups, which are increasingly turning their attention toward the operational technology (OT) that underpins a nation’s most vital services. These actors, though often less sophisticated than state-sponsored operatives, are demonstrating a dangerous willingness to cause tangible disruption, exploiting common security oversights to access systems controlling everything from water treatment to agricultural processes.
This article aims to provide a comprehensive overview of this emerging threat by addressing the most pressing questions surrounding these attacks. It will delve into the identity of the perpetrators, the methods they employ, and the specific vulnerabilities they exploit within critical infrastructure sectors. Furthermore, it will outline the immediate and long-term defensive strategies recommended by leading security agencies, offering clear guidance for organizations to fortify their defenses. Readers can expect to gain a deeper understanding of the risks posed by these opportunistic attacks and the crucial steps required to protect the essential services upon which society depends.
Key Questions or Key Topics Section
Who Are the Actors Behind These Attacks
The entities orchestrating these intrusions are not the covert, highly funded advanced persistent threat (APT) groups typically associated with nation-state espionage. Instead, the advisory identifies a consortium of pro-Russia hacktivist groups, including Cyber Army of Russia Reborn (CARR), Z-Pentest, NoName057(16), and Sector16. These groups operate more openly, often for ideological or political motivations, and seem to function within a collaborative ecosystem. They frequently amplify each other’s activities, share tactics, and jointly claim responsibility for attacks, creating a force multiplier effect that enhances their visibility and perceived impact.
This collaborative model allows for the rapid dissemination of successful attack methods, increasing the likelihood of widespread, copycat intrusions across various sectors. While their individual technical capabilities may be limited, their collective action and shared motivation present a persistent and unpredictable threat. Unlike APTs that often seek to remain undetected for long-term intelligence gathering, these hacktivists thrive on publicity, using social media to boast about their exploits and exaggerate their impact to sow fear and garner attention for their cause.
What Makes These Attacks a Significant Concern
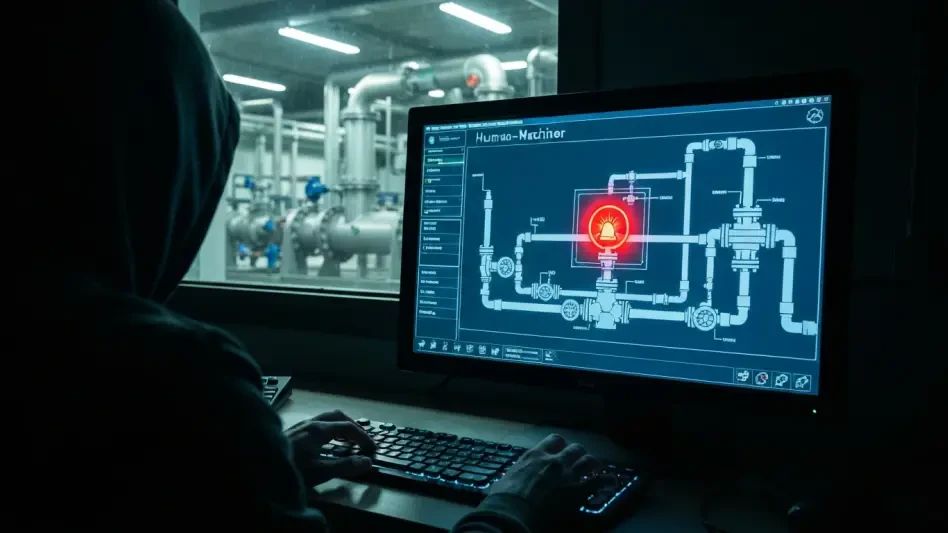
The primary concern stemming from these hacktivist campaigns is not their technical sophistication but their reckless intent combined with a profound lack of understanding of the systems they target. The advisory highlights that these actors often misunderstand the industrial processes they are attempting to disrupt. This ignorance is paradoxically what makes them so dangerous; they may not be able to execute a complex, multi-stage attack, but they are capable of blindly manipulating settings on a Human-Machine Interface (HMI) without appreciating the real-world consequences. Their goal is often simple disruption, but their actions could inadvertently trigger a cascade of failures with severe physical outcomes.
Moreover, the apparent disregard for human safety is deeply alarming. Attacks have been observed against occupied facilities, and while no injuries have been reported to date, the potential for harm remains significant. Disabling safety alarms or altering parameters in a water treatment plant or an energy facility could lead to hazardous conditions. The low barrier to entry for these attacks—requiring only basic tools and knowledge—means they can be replicated easily, creating a widespread risk that is difficult to quantify but impossible to ignore. The threat lies in the intersection of low-skill execution and high-impact potential.
Which Sectors Are Primarily at Risk
The advisory specifically calls out several critical infrastructure sectors as primary targets for these pro-Russia hacktivist groups, including water and wastewater systems, the food and agriculture sector, and energy facilities. These sectors are particularly attractive because of their direct impact on public health and safety, making any disruption highly visible and politically potent. A successful intrusion into a water utility, for example, could compromise water quality, while an attack on the food supply chain could create significant economic and social turmoil.
However, the vulnerability is not confined to these specific industries. The methodology employed by these groups—scanning the public internet for exposed devices—means that any organization utilizing OT systems with insecure, internet-facing components is a potential victim. The attacks are largely opportunistic rather than highly targeted, meaning the actors are hunting for the “low-hanging fruit” of cybersecurity. Consequently, any critical infrastructure entity that has not adequately secured its remote access points or segmented its OT network from its IT network remains at an elevated risk of becoming an unintentional target.
How Are These Intrusions Being Carried Out
The intrusion methodology is disturbingly simple, inexpensive, and easy to replicate, which contributes to its widespread adoption among these groups. The process typically begins with threat actors using common internet-scraping tools, such as Nmap or OPENVAS, to scan for devices with open Virtual Network Computing (VNC) ports, which are often used for remote administration. They focus on default ports like 5900 but also search nearby ports for any exposed services that might grant them access to a network.
Once a vulnerable device is identified, the attackers employ brute-force password spraying tools to gain entry, a technique that is highly effective against systems still using default, weak, or nonexistent passwords. Upon successfully authenticating, they gain direct access to HMI devices, which provide a graphical interface for monitoring and controlling industrial processes. From here, they can manipulate settings, alter parameters, disable alarms, or even shut down devices. To maximize their propaganda value, they meticulously document their actions through screen recordings and screenshots, which are later posted on social media platforms to showcase their capabilities and claim responsibility. In some instances, these intrusions are coupled with simultaneous Distributed Denial-of-Service (DDoS) attacks to create further chaos and potentially distract security teams from the more critical OT breach.
Mitigation and Response Strategies
What Immediate Steps Can Organizations Take
When an exposed system with weak credentials is discovered, organizations must operate under the assumption that it has already been compromised. The advisory stresses the need to immediately initiate incident response protocols to contain the threat and assess the damage. The first critical step is to isolate the potentially compromised hosts by either quarantining them within the network or taking them completely offline to prevent any further malicious activity or lateral movement by the threat actor.
Following isolation, a thorough threat-hunting process should begin to determine the full scope of the intrusion. This involves collecting and analyzing digital artifacts such as logs, running processes, unusual authentication events, and recent network connections to identify the attacker’s footprint. After the investigation, all compromised hosts should be reimaged from a known clean state, and all associated account credentials must be reset. Finally, it is crucial to report the compromise to the relevant authorities, such as CISA or the FBI, to contribute to the broader understanding of the threat and to receive further guidance on remediation.
What Are the Long Term Defensive Measures
Beyond immediate incident response, organizations must implement robust, long-term defensive measures to build resilience against future attacks. The cornerstone of this strategy is reducing the attack surface by minimizing the exposure of OT assets to the public internet. Organizations should leverage attack surface management tools and web-based search platforms to proactively identify and close any unauthorized or insecure connections within their IP ranges. Where internet connectivity is essential, access should be strictly controlled through firewalls and Virtual Private Networks (VPNs).
A mature asset management program is also critical, enabling organizations to map data flows and understand all access points into their OT environment. Network segmentation, which creates a secure barrier between IT and OT networks, is a fundamental control that can prevent an initial compromise in the corporate environment from spilling over into critical industrial systems. Furthermore, organizations must enforce robust authentication procedures, moving away from shared or default passwords, and ensure that all software and systems are kept up to date with the latest security patches. Finally, having and regularly practicing a comprehensive disaster recovery plan will ensure that operations can be restored quickly and safely in the event of a successful attack.
What Is the Role of Device Manufacturers in This Ecosystem
The responsibility for securing critical infrastructure does not lie solely with the asset owners and operators. A significant portion of the burden must be shouldered by the OT device manufacturers who design and build the technology. The joint advisory makes a strong call for manufacturers to adopt a “secure-by-design” and “secure-by-default” philosophy, embedding security into their products from the very beginning of the development lifecycle rather than treating it as an afterthought.
Specific recommendations for manufacturers include eliminating the use of default credentials, which are a primary target for attackers, and instead requiring users to create strong, unique passwords upon initial setup. They are also urged to mandate multi-factor authentication (MFA) for privileged users, provide robust logging capabilities at no additional cost, and publish a Software Bill of Materials (SBOMs) for their products. This transparency allows asset owners to better understand and manage the potential vulnerabilities within their systems. By taking ownership of the security outcomes for their customers, manufacturers can play a pivotal role in raising the baseline of security across the entire critical infrastructure landscape.
Summary or Recap
The current threat landscape reveals a significant and growing risk posed by pro-Russia hacktivist groups targeting global critical infrastructure. These actors, while not as technically advanced as traditional state-sponsored groups, leverage simple and opportunistic methods to exploit common security weaknesses, such as exposed VNC services and weak passwords. Their primary targets are vital sectors like water, energy, and agriculture, where disruption can have a direct and tangible impact on public life.
The core of the issue lies in the convergence of easily accessible OT systems and the reckless intent of attackers who often lack a full understanding of the industrial processes they are manipulating. In response, a multi-faceted defense is necessary. Organizations must prioritize reducing their internet attack surface, implementing strong network segmentation, and enforcing rigorous authentication policies. At the same time, a systemic shift is required from OT device manufacturers, who must embrace secure-by-design principles to build products that are inherently resilient against such threats, thereby raising the security posture of the entire ecosystem.
Conclusion or Final Thoughts
The joint security advisory on pro-Russia hacktivist activities served as a powerful reminder of how the lines between digital conflict and physical harm had become irrevocably blurred. The warnings issued by transnational agencies underscored the urgent reality that even relatively low-skill cyberattacks could precipitate tangible disruptions to the essential services that form the bedrock of modern society. It became evident that the opportunistic exploitation of basic security oversights was no longer a theoretical risk but an active and ongoing campaign with potentially severe consequences.
This shift in the threat landscape compelled a broader re-evaluation of cybersecurity, moving it from a purely technical IT concern to a fundamental component of national security and public safety. The incidents demonstrated that securing operational technology was not just about protecting data but about safeguarding physical processes and human well-being. Ultimately, the alarm raised by these agencies marked a critical juncture, highlighting that proactive defense, shared responsibility between operators and manufacturers, and a foundational commitment to security were the only viable paths forward in an increasingly contested digital world.