Password Forensics & Identity Compromise Recovery

Incident Response and Forensics
New SantaStealer Malware Hides in System Memory
A recently discovered malware strain, operating under a malware-as-a-service model, is providing cybercriminals with a powerful tool designed to function entirely within a computer's system memory, making it exceptionally difficult for traditional an...
Read More Incident Response and Forensics
Are Fake Government Apps Draining Your Bank Account?
A highly organized and large-scale cybercrime campaign known as NexusRoute is actively compromising Android devices across India by impersonating official government applications to steal sensitive financial and personal data.
Read More Incident Response and Forensics
Coupang Breach Exposes Dangers of Insider Threats
In a digital security failure of staggering proportions, South Korean e-commerce leader Coupang disclosed a data breach that compromised the personal information of over 33 million individuals, a figure representing nearly two-thirds of the nation’s...
Trending
Read More Incident Response and Forensics
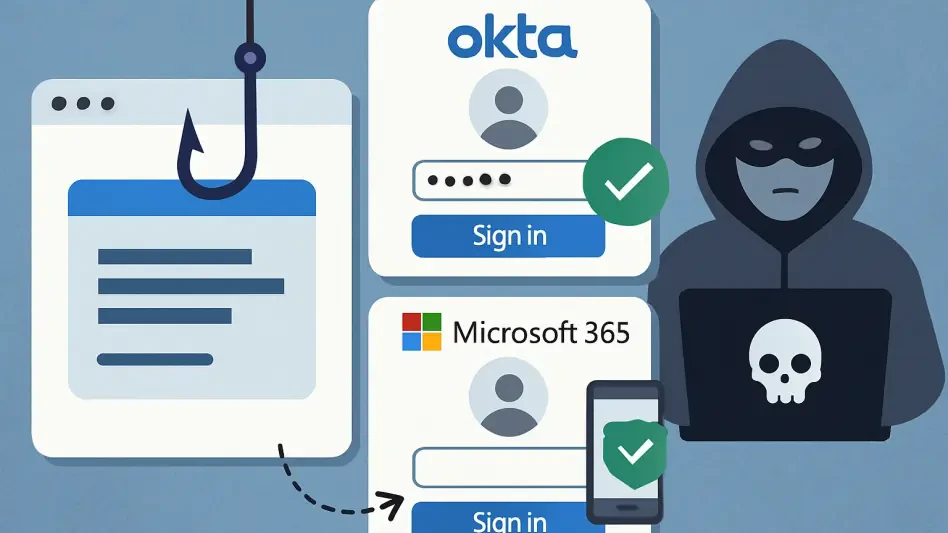
Phishing Attack Bypasses Okta and Microsoft 365 MFA
A recently uncovered and highly sophisticated Adversary-in-the-Middle phishing campaign is actively targeting organizations utilizing Microsoft 365 and Okta, successfully circumventing the multi-factor authentication protections that many businesses...
Read More Incident Response and Forensics
Is Your Mac at Risk From Malicious AI Chats?
The increasing integration of artificial intelligence into daily digital life has created a landscape where users confidently turn to AI chatbots for quick solutions, from drafting emails to troubleshooting technical issues on their computers.
Read More Incident Response and Forensics
AI Identity Theft Fears Grow Among UK Homebuyers
The already fraught process of purchasing a home in the United Kingdom has become burdened by a new and growing anxiety, as a recent survey reveals that 62 percent of consumers now fear their identity could be compromised by fraudsters using sophisti...
Trending
Read More Incident Response and Forensics
Is a 2FA Flaw Bypassing Your Cal.com Password?
In an era where two-factor authentication (2FA) is widely regarded as a fundamental layer of digital security, the discovery of a flaw that renders it ineffective can be particularly jarring for users who believe their accounts are adequately protect...
Read More Incident Response and Forensics
How Did One Stolen Car Unravel a Fraud Empire?
An unexpected letter arriving in a Bexar County mailbox set in motion a chain of events that would expose a sprawling and sophisticated identity theft ring operating in the heart of Texas.
Read More
Get our content freshly delivered to your inbox. Subscribe now ->
Receive the latest, most important information on cybersecurity.