Global Cyberattacks & Response

Human Factors in CyberSecurity
Interpol Fights the Threat of Weaponized AI
In a covert war waged across digital frontiers, the international criminal police organization is confronting an adversary that learns, adapts, and strikes with unprecedented sophistication.
Read More Cyberсrime and Cyber Warfare
Is Your SmarterMail Server a Gateway for Ransomware?
An otherwise routine business communication tool is increasingly being transformed into a dangerous entryway for cybercriminals, turning the daily flow of emails into a potential flood of ransomware.
Research Summary Read More Cyberсrime and Cyber Warfare
What Does This AI Hire Signal for Big Law?
In a move that reverberates across the legal industry, global law firm Norton Rose Fulbright has appointed Helen Christakos, a leading expert in privacy, artificial intelligence (AI), and cybersecurity, as a partner in its San Francisco office.
Read More Cyberсrime and Cyber Warfare
How Did UNC3886 Breach Singapore's Telecoms?
A highly sophisticated cyber espionage campaign, which remained undetected for nearly a full year, successfully infiltrated the core of Singapore's telecommunications sector by exploiting a series of previously unknown vulnerabilities in widely used...
Read More Cyberсrime and Cyber Warfare
Trend Analysis: African Cybersecurity Maturity
The catastrophic data breach in Senegal, which laid bare the biometric and personal information of a vast portion of the nation's adult populace, serves as a powerful and troubling signal for the entire continent.
Trend Analysis Read More Cyberсrime and Cyber Warfare
Is Your Windows PC Vulnerable to a One-Click Hack?
A single, seemingly innocent click on a link or the opening of a familiar document could be all it takes for malicious actors to seize complete control of a Windows PC, a startling reality brought to the forefront by the discovery of several critical...
Read More Cyberсrime and Cyber Warfare
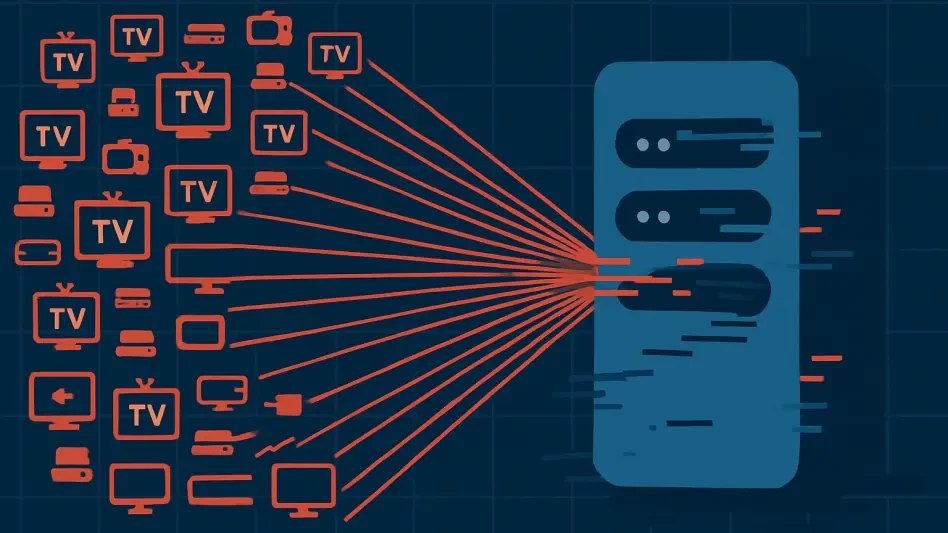
Streaming Boxes Used in Largest Ever Cyberattack
The seemingly innocuous streaming boxes that have become a common fixture in living rooms around the world have been unmasked as unwitting soldiers in a digital army, contributing to the largest distributed denial of service attack ever recorded.
Read More Cyberсrime and Cyber Warfare
Singapore Telcos Breached in State-Sponsored Cyberattack
A highly sophisticated and coordinated cyber espionage campaign successfully breached the networks of Singapore's four primary telecommunications providers—M1, SIMBA Telecom, Singtel, and StarHub—triggering a massive, 11-month national cyber defense...
Read More
Get our content freshly delivered to your inbox. Subscribe now ->
Receive the latest, most important information on cybersecurity.