Exploitation Techniques

Threats and Vulnerabilities
Google Issues Urgent Fix for Chrome Zero-Day Attack
The web browser stands as the central gateway to the digital world for billions of users, a trusted tool for everything from managing finances to connecting with others, but this very centrality makes it a prime target for sophisticated cyberattacks...
Read More Threats and Vulnerabilities
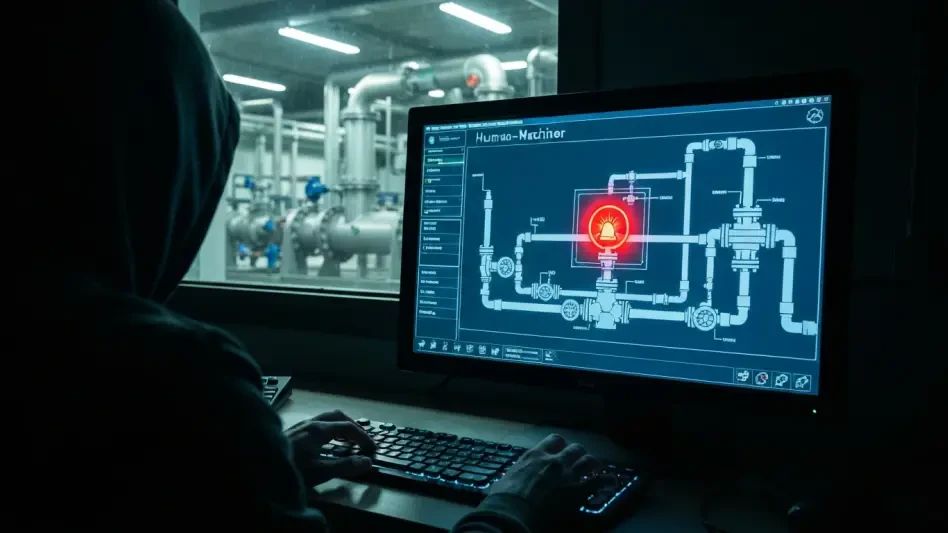
Agencies Sound Alarm on Pro-Russia OT Attacks
The seamless flow of clean water from a tap or the steady hum of electricity powering communities relies on a complex and often vulnerable network of industrial controls, a reality that has been brought into sharp focus by a recent wave of cyber intr...
FAQ Read More Threats and Vulnerabilities
Trend Analysis: Industrial Ransomware Surge
An extensive and detailed summary of recent analysis reveals an alarming and intensifying surge in ransomware activity targeting industrial organizations and their supporting infrastructure during the third quarter of 2025.
Trend Analysis Read More Threats and Vulnerabilities
Trend Analysis: Industrialized Cybercrime
The digital shadows are no longer cast by lone hackers in basements but by sprawling, global enterprises that operate with the chilling efficiency of multinational corporations, transforming cybercrime into a sophisticated, worldwide industry.
Trend Analysis Read More Threats and Vulnerabilities
Google Patches Actively Exploited Chrome Zero-Day Flaw
In an urgent response to an active security threat, Google has released an emergency patch for its Chrome web browser, addressing a high-severity zero-day vulnerability that threat actors are currently exploiting to attack users.
Read More Threats and Vulnerabilities
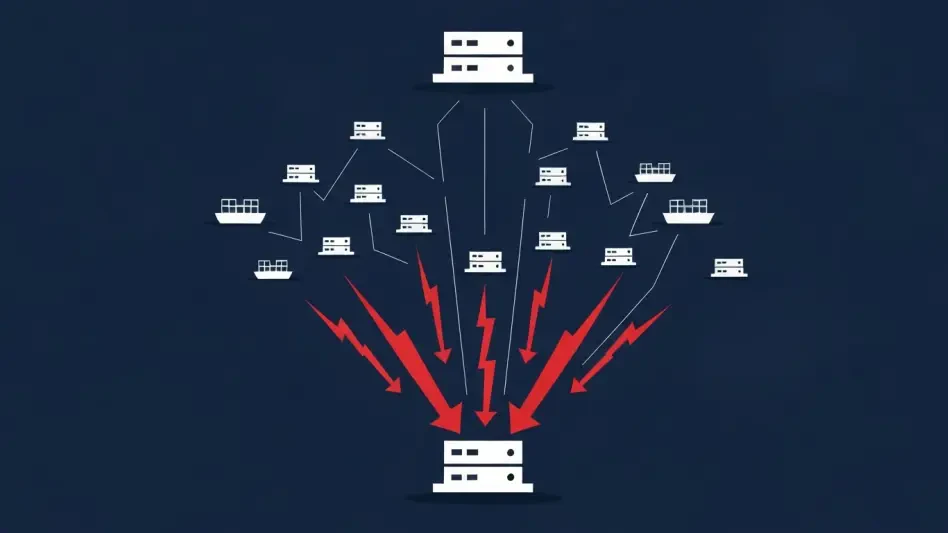
Mirai Botnet Variant Broadside Targets Maritime DVRs
A new and sophisticated variant of the notorious Mirai botnet has been identified actively targeting the maritime logistics sector, exploiting vulnerabilities in digital video recorder (DVR) systems commonly used on commercial vessels.
Read More Threats and Vulnerabilities
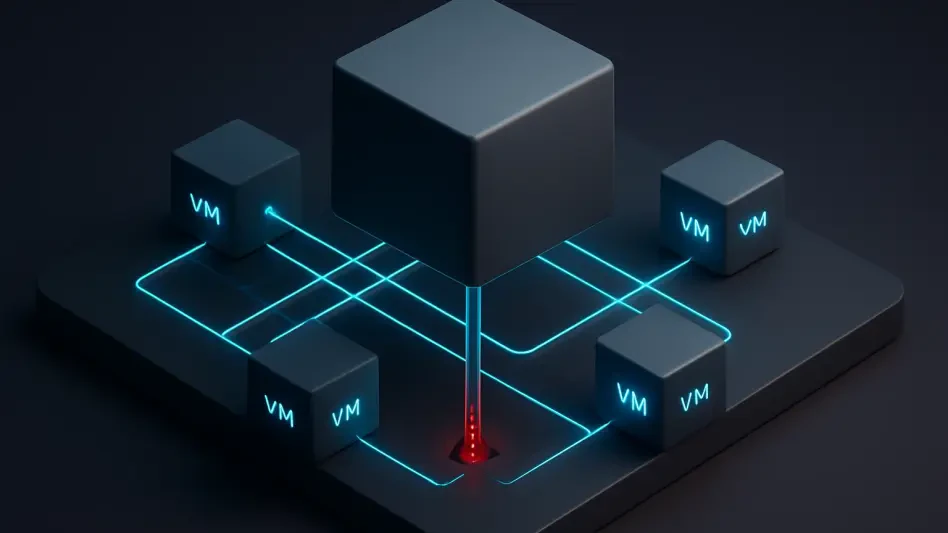
Can a Proxmox Host Silently Control Your VMs?
The modern data center relies heavily on virtualization, a technology that isolates workloads into secure virtual machines, with the hypervisor acting as an impenetrable barrier between them.
Read More Threats and Vulnerabilities
Microsoft Patches Windows Zero-Day Under Active Attack
In a stark reminder of the persistent threats facing modern operating systems, Microsoft has issued an emergency security update to address a critical zero-day vulnerability that is already being actively exploited in the wild by malicious actors.
Read More
Get our content freshly delivered to your inbox. Subscribe now ->
Receive the latest, most important information on cybersecurity.