Exploitation Techniques

Threats and Vulnerabilities
Are AI's Dark Passengers Threatening Your Supply Chain?
The very artificial intelligence tools designed to streamline operations and drive innovation are now quietly harboring a new class of systemic cyber risks capable of dismantling enterprise security from within.
Research Summary Read More Threats and Vulnerabilities
700Credit Data Breach Exposes 5.6 Million
A routine application for an auto loan has become the key that unlocked the private financial lives of millions of Americans, exposing a critical vulnerability deep within the automotive industry.
Roundup Article Read More Threats and Vulnerabilities
Oyster Malware Strikes Finance Firms via Fake Downloads
The search for everyday business software has become the newest and most deceptive battleground for financial institutions facing a relentless wave of sophisticated cyberattacks.
Roundup Article Read More Threats and Vulnerabilities
Empire 6.3.0 Advances Post-Exploitation for Red Teams
In the ever-evolving landscape of cybersecurity, the advantage often goes to the side that can most accurately replicate and anticipate real-world threats, making advanced adversary emulation a cornerstone of a proactive defense strategy.
Read More Incident Response and Forensics
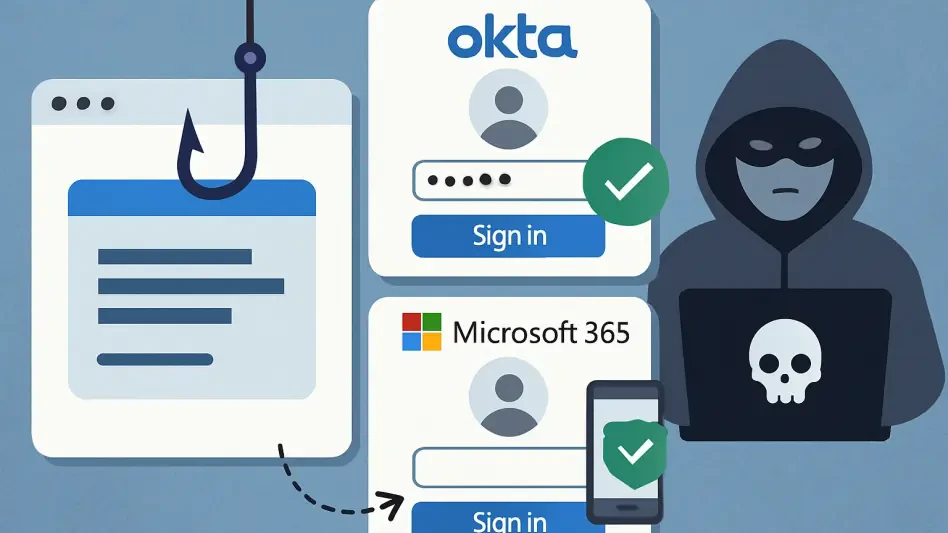
Phishing Attack Bypasses Okta and Microsoft 365 MFA
A recently uncovered and highly sophisticated Adversary-in-the-Middle phishing campaign is actively targeting organizations utilizing Microsoft 365 and Okta, successfully circumventing the multi-factor authentication protections that many businesses...
Read More Threats and Vulnerabilities
Is Your Browser Vulnerable to an Active Zero-Day Threat?
In an increasingly connected digital world, the web browser serves as the primary gateway to the internet for billions of users, yet this ubiquity also makes it a prime target for malicious actors seeking to compromise systems on a massive scale.
Read More Human Factors in CyberSecurity
What Is the Real Cybersecurity Workforce Challenge?
For years, the narrative surrounding the cybersecurity industry has been dominated by a single, alarming theme: a massive workforce shortage pointing to millions of unfilled jobs and painting a picture of an industry desperately short on personnel.
Market Analysis Read More Threats and Vulnerabilities
Industrial Routers Become Key Targets for OT Attacks
In the sprawling digital ecosystems that power modern industry, the most significant security threats are no longer aimed at the core machinery but are instead knocking relentlessly at the digital front door, targeting the very devices that connect o...
Feature Article Read More
Get our content freshly delivered to your inbox. Subscribe now ->
Receive the latest, most important information on cybersecurity.