Cyber Espionage Techniques

Cyberсrime and Cyber Warfare
Is Your Windows PC Vulnerable to a One-Click Hack?
A single, seemingly innocent click on a link or the opening of a familiar document could be all it takes for malicious actors to seize complete control of a Windows PC, a startling reality brought to the forefront by the discovery of several critical...
Read More Cyberсrime and Cyber Warfare
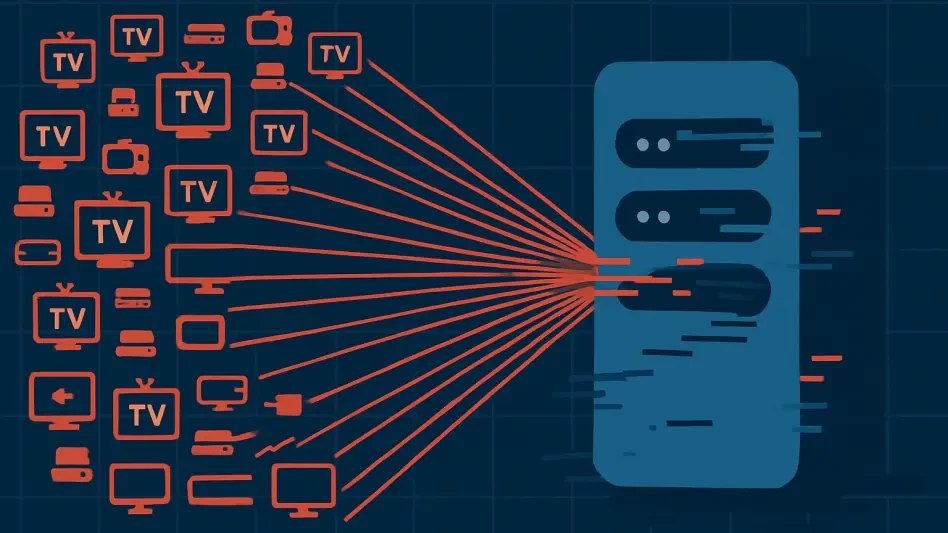
Streaming Boxes Used in Largest Ever Cyberattack
The seemingly innocuous streaming boxes that have become a common fixture in living rooms around the world have been unmasked as unwitting soldiers in a digital army, contributing to the largest distributed denial of service attack ever recorded.
Read More Cyberсrime and Cyber Warfare
Singapore Telcos Breached in State-Sponsored Cyberattack
A highly sophisticated and coordinated cyber espionage campaign successfully breached the networks of Singapore's four primary telecommunications providers—M1, SIMBA Telecom, Singtel, and StarHub—triggering a massive, 11-month national cyber defense...
Read More Cyberсrime and Cyber Warfare
Trend Analysis: Cybersecurity Threat Landscape
While high-stakes ransomware attacks capture headlines and dominate public fear, a surprising revelation from Federal Trade Commission (FTC) data shows they are merely a whisper in the storm of reported consumer fraud.
Trend AnalysisTrending
Read More Cyberсrime and Cyber Warfare
Could a Default Password Take Down a Power Grid?
A recent cyberattack that brought Poland's energy grid to the brink of a widespread blackout serves as a stark reminder that the security of national infrastructure can hinge on something as simple as a factory-set password.
Industry Report Read More Cyberсrime and Cyber Warfare
Is Economic Spying The New Face Of Cyber Warfare?
In the shadowed corridors of international relations, the rules of engagement are being rewritten not by treaties, but by keystrokes, as state-sponsored cyber operations increasingly pivot from traditional military reconnaissance to a far more insidi...
Read More Threats and Vulnerabilities
Lotus Blossom Deploys Chrysalis Backdoor via Notepad++
In the complex digital ecosystem where trust is a currency, the very tools designed to build and create can be twisted into weapons of espionage, turning a developer's trusted companion into an unseen spy.
Read More Cyberсrime and Cyber Warfare
How Did a Software Flaw Expose the EU Commission?
The very software designed to fortify thousands of government mobile devices against intrusion became the unlocked door through which attackers compromised the European Commission’s central command, revealing a critical vulnerability at the heart of...
Feature Article Read More
Get our content freshly delivered to your inbox. Subscribe now ->
Receive the latest, most important information on cybersecurity.