In an increasingly digital world, smartphones are extensions of users’ lives, relaying personal, professional, and financial information every day. With this convenience comes a growing responsibility to secure these devices against unauthorized access. Many iPhone users overlook or underestimate the vulnerabilities their habits may create, potentially opening doors to cyber threats. A keen understanding of these habits and the adoption of prudent security measures are imperative to safeguard personal data and maintain privacy. As technology advances, so does the sophistication of cyber threats, underscoring the necessity for users to remain vigilant and proactive in securing their devices.
Mitigating Bluetooth and Location Access Risks
Limiting Bluetooth Usage
Bluetooth technology, while beneficial, can become a gateway for unauthorized access if not properly managed. With widespread use, from connecting headphones to syncing fitness trackers, it is essential to discern where its use is justified and where caution is warranted. When Bluetooth stays perpetually activated, it potentially exposes the device to trackers and malicious attempts to gather data from nearby devices. To mitigate these risks, users must restrict Bluetooth functionality to essential applications and devices only, manually disabling it when not in use. This simple preventive measure becomes a formidable barrier against data collection attempts, protecting users’ privacy.
Additionally, Bluetooth vulnerabilities may often be exploited by sophisticated hackers intent on gleaning information from unsuspecting users. Users should avoid connecting to unknown or unverified devices, as they might be a source of ransomware or malware. Regular checking and updating of the device’s OS can address any identified vulnerabilities that malicious actors might otherwise exploit. Heightened awareness, paired with a few technical precautions, significantly reduces the potential for security breaches, showcasing the dual importance of awareness and action.
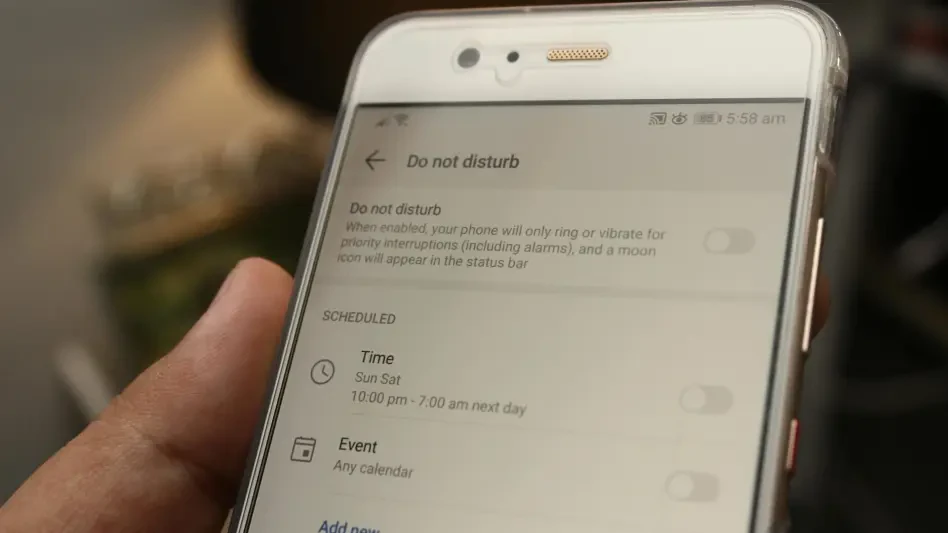
Managing Location Services
Control over location services is equally crucial in the digital era, given the premium placed on geo-data by developers and advertisers. Many apps request perpetual access to location information, often without a clearly defined need. While navigation and mapping services require pinpoint accuracy, most other apps overreach in their information-gathering endeavors. Users should routinely audit the list of apps with location access, modifying settings to allow tracking only when the application is in use or denying access entirely where unjustified. This approach minimizes unnecessary location data dissemination, offering better control over personal information.
Moreover, indiscriminate location sharing can create activity patterns open to exploitation by cybercriminals and advertisers alike. iPhone users should resist the allure of convenience over security by denying or limiting location permissions. This approach disrupts profitable data streams, ensuring personal movements and routines remain protected and less susceptible to targeting. Increased control over location data complements other security practices, reinforcing a holistic stance against unauthorized monitoring and potential breaches.
Strengthening Password Protocols
Password Managers and Complexity
The practice of using strong passwords is an essential strategy for fortifying personal data against unauthorized access. With multiple accounts and platforms requiring authentication, relying on simple or repeated passwords greatly undermines security efforts. Hackers employing advanced techniques can swiftly compromise these simplistic defenses. Users are thus encouraged to adopt password managers, digital tools designed to generate, retrieve, and store complex passwords securely. By offloading the responsibility of remembering numerous credentials, these applications enhance protection without compromising convenience.
Utilizing a diverse array of letters, numbers, and symbols when forming passwords reduces predictability and makes them more challenging to crack. Password managers typically advise and even generate passwords with these characteristics, offering an intuitive solution to what is, for many, a cumbersome task. Implementing these tools as part of regular cybersecurity hygiene fortifies security measures, protecting user accounts from infiltration attempts that capitalize on weak password structures.
Two-Factor Authentication
Two-factor authentication (2FA) introduces an additional verification step that significantly bolsters security for sensitive accounts. Deploying this measure on financial accounts, emails, and any service containing personal information delivers an extra layer of protection beyond the password alone. 2FA incorporates a second factor, often a temporary code sent to a trusted device, effectively shutting down unauthorized access even if login credentials are compromised.
Emerging threats underscore the necessity of this method, as cyber actors adapt constantly to bypass conventional defenses. By mandating a second layer of verification, users impede unauthorized access more comprehensively. Although it may require small additional steps during logins, the assurance it provides makes it an indispensable safety measure. Incorporating 2FA into regular security routines stands as a decisive step in curbing breaches and protecting valuable personal information.
Advancing Personal Data Security
In our increasingly digital world, smartphones have become integral to our daily lives, serving as the conduits for personal, professional, and financial exchanges. This convenience demands a critical responsibility to protect these devices from unauthorized access and cyber threats. However, many iPhone users fail to recognize or underestimate the risks their daily habits may pose, inadvertently inviting exploitation. Understanding these potential vulnerabilities and adopting sound security practices is essential to preserve personal information and ensure privacy. As technology relentlessly progresses, so does the complexity and sophistication of cyber threats. This evolution highlights the urgent need for users to remain alert, regularly update security measures, and be proactive in defending their devices. Investing time to comprehend the nuances of digital security can make all the difference in safeguarding vital information and mitigating the risks posed by today’s ever-evolving digital landscape.