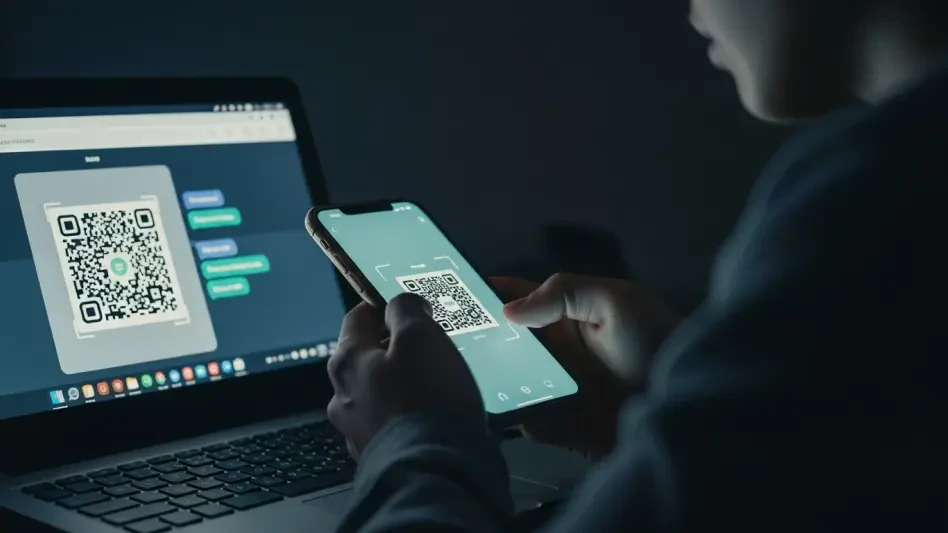
That seemingly harmless black-and-white square you scan for a restaurant menu or a quick payment now serves as a potential gateway for sophisticated cybercriminals. In a world that runs on contactless convenience, QR codes have become an unverified gateway, creating a new and rapidly growing attack surface for social engineering scams. The speed and ease that made them a global standard have also made them an ideal tool for threat actors who rely on deception over complex code. This analysis will explore the rise of QR code-based attacks, dissect the methods used by hackers, provide expert insights on mitigation, and examine the future of this evolving threat.
The Surge of QR Codes and the Quishing Epidemic
From Pandemic Necessity to Daily Habit
The global adoption of QR codes has skyrocketed since 2020, transforming them from a niche marketing tool into an essential part of daily life for payments, information access, and authentication. This explosion in usage, however, has been shadowed by a parallel rise in malicious activity. Security bodies like Germany’s BSI and BfV have issued warnings about a significant uptick in “Quishing” (QR code phishing) incidents. These campaigns are no longer random; they are increasingly targeted, with state-backed actors aiming to compromise the accounts of high-profile individuals, including military leaders, diplomats, and journalists.
This trend highlights a critical vulnerability: as the public becomes more accustomed to scanning QR codes without a second thought, their natural suspicion declines. Hackers have capitalized on this trust, embedding malicious links into seemingly legitimate codes placed on everything from parking meters to promotional flyers. The result is a widespread threat that affects both the general public and strategically important targets, turning everyday convenience into a security liability.
Deconstructing the Scams
A prominent case study involves a sophisticated social engineering campaign targeting users of the Signal messenger app. State-backed hackers, rather than deploying complex malware, have exploited the app’s standard features to spy on private conversations. These attackers leverage human psychology, understanding that a well-crafted, urgent message is often more effective than a technical exploit. By bypassing traditional security defenses, they go straight for the weakest link: the user.
One common method is “The Fake Support Scam,” where attackers impersonate official support teams. They contact a target with a direct message, often through an automated chatbot, claiming a severe security breach requires immediate action. This manufactured urgency pressures the user into sharing a six-digit verification code or their secret PIN. Once the attacker has this information, they can register the victim’s account on their own device, locking the true owner out and gaining full control to send messages or spread disinformation.
A more subtle technique is “The QR Code Trap.” In this scenario, the attacker engages the target with a plausible story, convincing them to scan a QR code to access a document or join a private group. In reality, scanning the code links the attacker’s device—such as a laptop or tablet—to the victim’s account. This method is particularly insidious because the victim can still use their account normally, completely unaware that a spy now has access to their recent chat history and all incoming messages in real time.
Expert Commentary: The Human Element in Digital Exploitation
Security experts emphasize that the remarkable success of Quishing scams lies in their masterful use of social engineering. These attacks prey on established human behaviors and cognitive biases. We are conditioned to trust official-looking alerts and follow instructions from what appear to be legitimate authorities. The QR code itself is a symbol of modern efficiency, and its perceived innocence makes it an incredibly effective Trojan horse for malicious intent.
The psychological manipulation is a key component of the attack. By creating a sense of urgency or offering a tempting reward, hackers bypass a person’s rational decision-making process. The very nature of the QR code—a block of pixels whose destination is hidden—forces a user to act on faith. This leap of faith is precisely what attackers exploit. Authorities reinforce a critical warning: official support channels, such as those for Signal, will never initiate contact to ask for a PIN or verification code via a direct message.
The Future of QR Code Security: Challenges and Countermeasures
As technology evolves, so will the threats associated with it. Future QR code attacks may integrate AI-driven chatbots to create even more convincing and personalized scams, making them harder to detect. Furthermore, attackers could increasingly target corporate networks by tricking employees into scanning malicious codes on their personal devices, which are often connected to internal systems. This blend of personal and professional vulnerability creates a significant risk for organizations.
The primary challenge in defending against Quishing remains the same: a QR code’s destination is invisible to the naked eye. This inherent lack of transparency makes it difficult for users to verify its safety before scanning. Therefore, the most effective defense is a combination of technological safeguards and user education. It is crucial to foster a healthy sense of skepticism toward unsolicited QR codes, especially those received in unexpected messages or found in public places.
To mitigate these risks, users must adopt critical defensive strategies. Regularly auditing the “Linked Devices” section in messaging apps and removing any unrecognized entries can sever an attacker’s access. Enabling advanced security features, such as a Registration Lock or a secret PIN, adds a vital layer of protection that can prevent an account takeover even if a verification code is compromised.
Conclusion: Fostering a Culture of Digital Vigilance
The convenience of QR codes was effectively weaponized by threat actors, transforming a tool of efficiency into a vector for intrusion and espionage. This trend demonstrated that user awareness and proactive caution have become more critical than ever in safeguarding personal and professional information. The core issue was not a failure of complex technology but a clever exploitation of fundamental human trust. To navigate the evolving digital landscape safely, it became essential to “Scan with Skepticism” and adopt a proactive security posture.