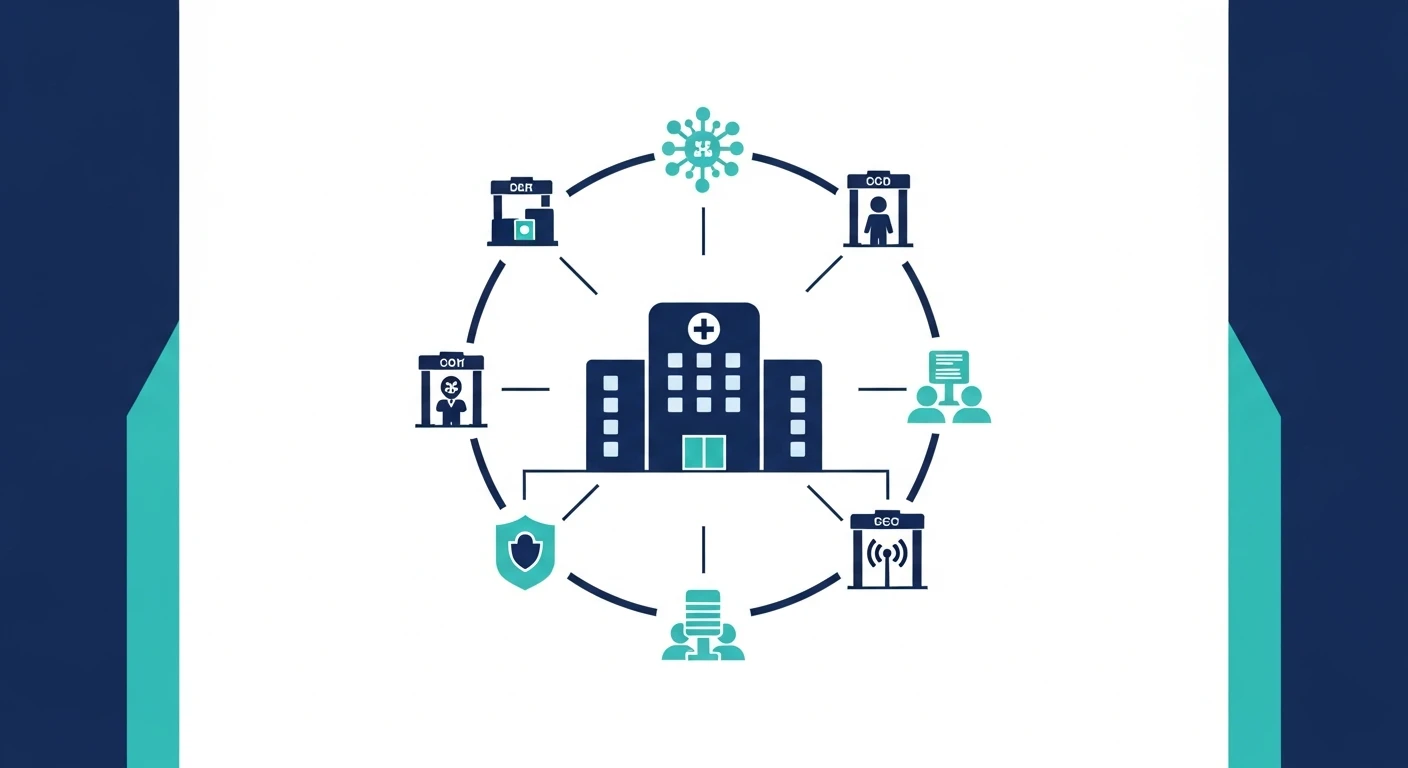
How Can Modern Access Governance Enable Business Growth?
The traditional image of a security guard standing behind a heavy desk with a physical logbook is rapidly being replaced by sophisticated digital ecosystems that prioritize operational agility just as…
Read More