
Woburn, MA — December 6, 2021 — According to Kaspersky’s 2021 Healthcare report, only 22% of global healthcare organizations confirmed that all medical equipment they utilize runs up to date software, with 73% saying that they continue to use legacy operating systems (OS). These findings highlight that many healthcare organizations are leaving themselves exposed to vulnerabilities and cyber-risks by running on outdated OS.
The survey results also found that organizations widely use medical equipment with a legacy OS mainly because of high upgrade costs, compatibility issues, or a lack of internal knowledge on how to upgrade, among other reasons.
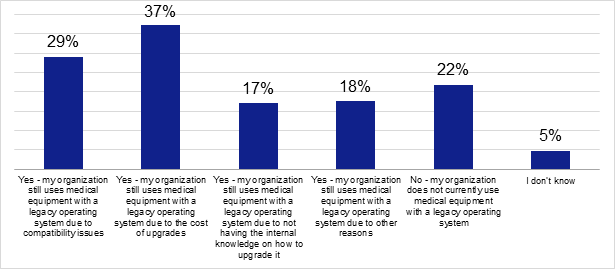
Does your organization currently use medical equipment with a legacy operating system, and if so, what are the main reasons for this?
The usage of outdated equipment leaves healthcare organizations vulnerable to cyber-incidents. When software developers stop supporting a system, they also halt the release of any updates that often contain security patches for discovered vulnerabilities. If left unpatched, these can become an easy and accessible initial attack vector to penetrate the company’s infrastructure, even for unskilled attackers. Healthcare organizations collect a wealth of sensitive and valuable data, making them one of the most lucrative targets, and unpatched devices can facilitate a successful attack for adversaries.
When it comes to cybersecurity readiness, only 30% of healthcare workers are very confident that their organization can effectively stop all security attacks or breaches at the perimeter. Just 34% expressed conviction that their organization has up to date, adequate hardware and software IT security protection.
At the same time, half (50%) of global respondents agreed that their organization had already experienced data leaks, DDoS or ransomware attacks.
“The healthcare sector is evolving to meet the demand for accessible help by actively adopting connected devices, but this also adds unique cybersecurity challenges typical to the embedded systems,” comments Sergey Martsynkyan, vice president of corporate product marketing at Kaspersky. “Our report confirms that many organizations still use medical devices that run on old OS and face obstacles that hamper upgrades. While there is a need for developing a strategy of modernization, there are also solutions and measures available which can help to minimize the risks in the meantime. Those combined with medical staff awareness can significantly raise the security level and pave the way for the future development of the healthcare industry.”
To help the healthcare sector minimize the likelihood of cyber-incidents caused by obsolete and unpatched systems, Kaspersky recommends taking the following steps:
- Provide your staff with basic cybersecurity hygiene training, as many attacks start with phishing or other social engineering techniques.
- Carry out a cybersecurity audit of your networks and remediate any weaknesses discovered in the perimeter or inside the network.
- Install anti-APT and EDR solutions, enabling threat discovery and detection, investigation, and timely remediation of incidents capabilities. Provide your SOC team with access to the latest threat intelligence and regularly upskill them with professional training. All of the above is available within Kaspersky’s Expert Security framework.
- Along with proper endpoint protection, dedicated services can help defend against high-profile attacks. Managed Detection and Response services can help identify and stop attacks in their early stages before the attackers achieve their goals.
- Harden embedded systems in medical devices that are rarely updated. Kaspersky Embedded System Security was designed to operate effectively even on low-end and legacy hardware and old software without overloading the system. The latest update of the solution includes cloud-based management capabilities allowing the control of embedded devices via the same hosted console as other endpoints.
More insights on the current state of the healthcare industry are available in the report.
