BRATISLAVA, MONTREAL — September 21, 2023 — ESET researchers have analyzed two campaigns by the Iran-aligned OilRig APT group: Outer Space from 2021, and Juicy Mix from 2022. Both of these cyberespionage campaigns targeted Israeli organizations exclusively, which is in line with the group’s focus on the Middle East, and both used the same playbook: OilRig first compromised a legitimate website to use as a C&C server and then delivered previously undocumented backdoors to its victims while also deploying a variety of post-compromise tools mostly used for data exfiltration from the target systems. Specifically, they were used to collects credentials from Windows Credential Manager and from major browsers, credentials, cookies and browsing history.
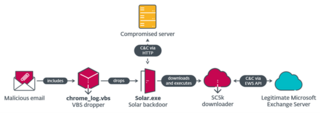
In their Outer Space campaign, OilRig used a simple, previously undocumented C#/.NET backdoor ESET Research has named Solar, along with a new downloader, SampleCheck5000 (or SC5k), that uses the Microsoft Office Exchange Web Services API for C&C communication. For the Juicy Mix campaign, the threat actors improved on Solar to create the Mango backdoor, which possesses additional capabilities and obfuscation methods. Both backdoors were deployed by VBS droppers, presumably spread via spearphishing emails. In addition to detecting the malicious toolset, ESET has also notified the Israeli CERT about the compromised websites.
ESET named the Solar backdoor based on the use of an astronomy-based naming scheme in its function names and tasks; we named Mango, another new backdoor, based on its internal assembly name and its filename.
Solar backdoor possesses basic functionalities and can be used, among other things, to download and execute files, and automatically exfiltrate staged files. An Israeli human resources company’s web server, which OilRig compromised at some point prior to deploying Solar, was used as the C&C server.
For its Juicy Mix campaign, OilRig switched from the Solar backdoor to Mango. It has a similar workflow to Solar and overlapping capabilities, with some notable technical changes. ESET identified an unused detection evasion technique within Mango. “This technique’s goal is to block endpoint security solutions from loading their user-mode code hooks via a DLL in this process. While the parameter was not used in the sample we analyzed, it could be activated in future versions,” says ESET researcher Zuzana Hromcová, who co-analyzed the two campaigns of OilRig.
OilRig, also known as APT34, Lyceum, or Siamesekitten, is a cyberespionage group that has been active since at least 2014 and is commonly believed to be based in Iran. The group targets Middle Eastern governments and a variety of verticals, including chemical, energy, financial and telecommunications.
For more technical information about OilRig and its Outer Space and Juicy Mix campaigns, check out the blogpost “OilRig’s Outer Space and Juicy Mix: Same ol’ rig, new drill pipes” on WeLiveSecurity. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.